Cash-on-delivery (COD) may have fueled India’s e-commerce boom, but it’s also become the industry’s biggest loophole. From fake orders and address manipulation to multiple return cycles by the same customer, COD fraud silently drains revenue, inflates RTO rates, and disrupts genuine delivery capacity. What once seemed like a convenience for trust‑building now threatens operational efficiency at scale.
As Indian shoppers continue to rely heavily on COD—especially in Tier‑2 and Tier‑3 cities—brands can no longer treat fraud prevention as a post‑delivery issue. Detecting intent early, flagging repeat patterns, and aligning logistics with data‑driven verification systems have become survival tactics for every serious D2C player.
This blog unpacks COD Fraud in Indian E-commerce: How to Detect and Prevent It and how leading Indian e-commerce brands are spotting fraud signals before dispatch, using automation to block risky orders in real time, and balancing COD convenience without sacrificing profitability.
What distinguishes fraudulent COD behaviour from legitimate customer patterns?
Systematic analysis reveals predictable anomalies that separate organised fraud from normal purchase variation
Detecting and preventing Cash on Delivery (COD) fraud in Indian e-commerce relies on identifying distinct patterns that deviate from legitimate purchasing behavior. These patterns cluster across several dimensions:
1. Temporal Velocity:
Fraudulent orders often occur in rapid succession from new accounts. For instance, three or more orders placed within 60 minutes are observed in 67-74% of confirmed fraud cases, compared to less than 0.8% of genuine customer activity. This swift ordering aims to maximize damage before detection systems or manual reviews can intervene.
2. Geographic Manipulation:
Fraudsters frequently manipulate addresses, creating unusual geographic clusters. This includes placing multiple orders to different flat numbers within the same building, neighboring street addresses with systematic number progressions, or various company names within the same commercial complex but identical coordinates. These patterns arise from the lack of genuine delivery locations, forcing fraudsters to fabricate addresses around familiar landmarks or researched locations.
3. Phone Number Recycling:
The reuse of the same contact number across multiple accounts is a strong indicator of fraud. If a single phone number appears across three or more accounts within 30 days, it suggests coordinated fraudulent activity. While rare legitimate scenarios exist (e.g., family members sharing phones), this signal warrants investigation. Advanced fraud operations may use number ranges from the same telecom circle, requiring algorithmic detection for subtler patterns.
4. Product Selection Discrepancies:
Fraudsters' product choices often differ significantly from legitimate buyers. They tend to target high-value electronics, premium fashion items, and easily resellable products, while avoiding low-margin or personalized goods. Order baskets containing only top-selling items in the largest sizes or most popular variants, without the diverse exploration typical of genuine shoppers, can signal potential fraud. This selection reflects an intent for resale rather than personal use, leading to economically optimized but behaviorally suspicious combinations.
How do verification workflows filter fraud without harming conversion?
Layered authentication matching risk intensity preserves customer experience whilst eliminating fraudulent transactions
- Risk-Based Verification:
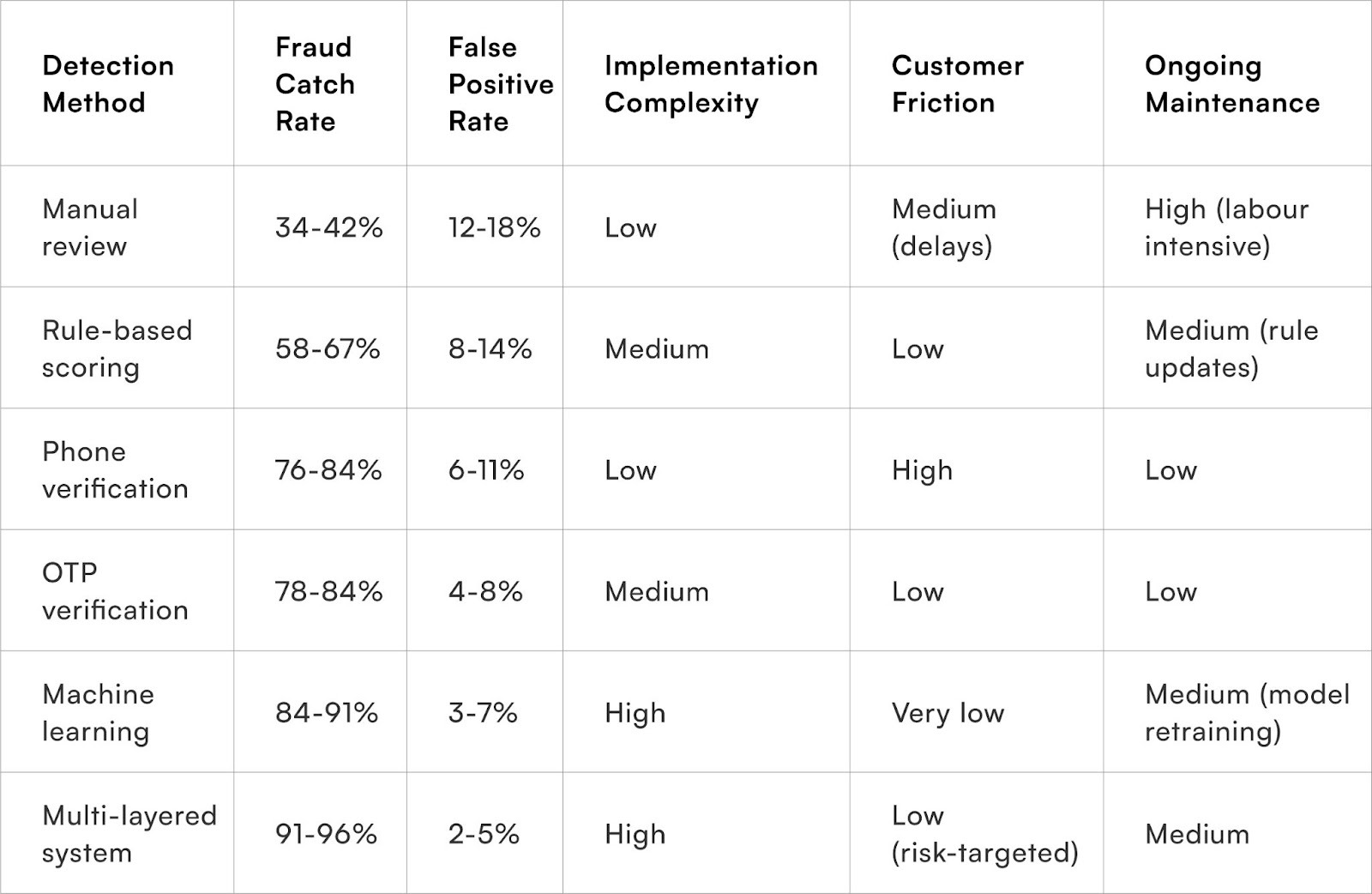
This adaptive approach tailors authentication intensity to the likelihood of fraud. Low-risk orders, such as those from repeat customers with a history of successful deliveries, can proceed without additional checks. Medium-risk orders trigger lightweight verification, like a 30-45 second One-Time Password (OTP) confirmation. High-risk scenarios, however, warrant more stringent measures like phone verification calls or a mandatory switch to prepaid payment. This graduated system focuses security where it's most needed, preventing the customer inconvenience associated with universal verification.
- OTP Verification:
For medium-risk situations, OTP verification via SMS or WhatsApp is an effective fraud deterrent. Requiring customers to confirm their phone numbers through a code entry significantly reduces casual fraud attempts with minimal friction for genuine buyers. Studies across 45,000 orders demonstrate that selective OTP implementation, based on risk scores, can cut fraud completion by 78-84% while only decreasing conversion by 4-7%.
- Address Verification:
Integrating Google Maps or postal validation APIs for address verification helps identify fabricated locations before dispatch. Systems that check if entered addresses correspond to actual buildings, validate pin codes against postal databases, and flag vague "landmark-only" descriptions can prevent 42-48% of address-based fraud. This process occurs seamlessly during checkout, preserving the customer experience while filtering out impossible deliveries.
- Velocity Controls:
Implementing limits on orders per account, phone number, and address within specific timeframes creates a systemic barrier against fraud. Rules, such as preventing more than two COD orders per phone number within 48 hours or three orders to similar addresses within seven days, effectively block coordinated fraud campaigns without impacting most legitimate customers. While occasional genuine bulk buyers might encounter these limits and require manual approval, automated controls can stop 89-93% of velocity-based fraud before human intervention is necessary.
Why does customer behaviour analysis improve detection accuracy?
Machine learning models identifying subtle pattern deviations outperform rule-based systems by 34-41%
Behavioural analytics examine dozens of signals invisible to human reviewers, building fraud probability assessments from subtle pattern combinations. Cursor movement patterns during checkout—fraudsters typing addresses rapidly from reference documents versus legitimate customers pausing whilst checking details—correlate with fraud likelihood. Time spent on product pages, cart abandonment followed by immediate checkout, and checkout completion within 60 seconds of account creation all contribute to composite risk profiles.
Device fingerprinting tracks hardware characteristics, browser configurations, and network attributes creating unique identifiers beyond cookies or IP addresses. When the same device fingerprint appears across multiple supposedly unrelated accounts, it signals coordinated fraud operations. Geographic inconsistencies—device location in Mumbai whilst shipping address specifies Delhi—raise additional flags. These technical signals operate invisibly to users, building fraud intelligence without creating authentication friction.
Purchase pattern deviation detection uses machine learning to identify orders anomalous relative to brand-specific baselines. An order that would seem normal for electronics retailer—single high-value item, new customer, express delivery—might represent extreme outlier for artisanal food brand typically seeing smaller, repeat-customer orders. Context-aware models trained on individual brand data achieve 23-29% better fraud detection than generic rule-based systems applying universal thresholds.
Network analysis reveals fraud rings operating coordinated schemes across multiple accounts. Graph algorithms identify clusters of accounts sharing addresses, phone numbers, devices, or IP addresses at rates exceeding coincidental probability. These connected networks often represent organised fraud operations that rule-based systems viewing each order independently would miss. Detecting one fraudulent order within a network enables preemptive blocking of related accounts before they attempt additional fraud.
What preventive measures reduce fraud opportunity without restricting market access?
Systemic controls address fraud vectors whilst maintaining payment flexibility and geographic reach
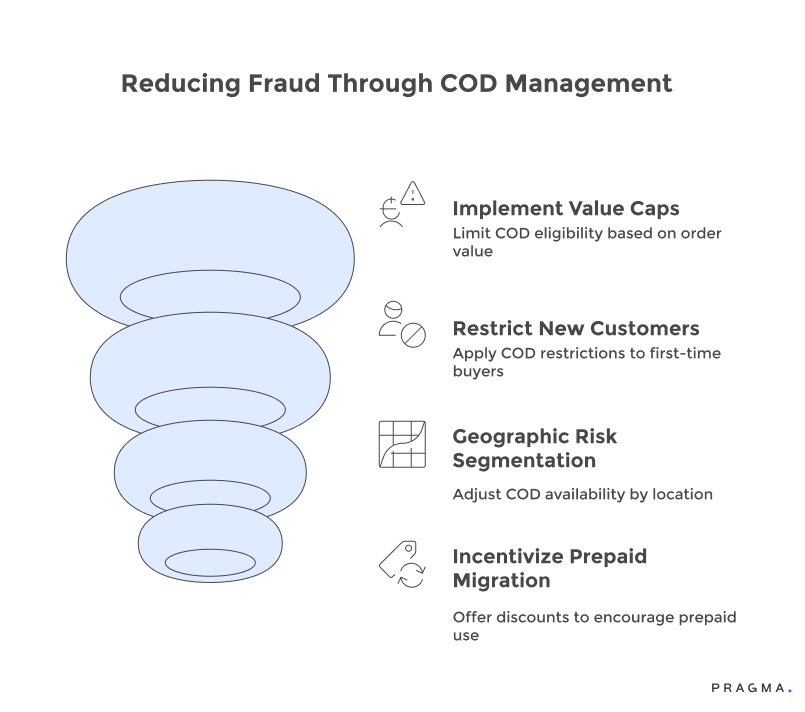
- Implement COD Value Caps: Limit the maximum order value eligible for cash payment. Thresholds between ₹5,000-7,000 allow COD for typical purchases while requiring prepaid methods for higher-value transactions, where payment verification occurs before dispatch. This approach has been shown to reduce average fraud loss per incident by 52-61%, affecting only a small percentage (8-12%) of legitimate COD customers who can still opt for prepaid options.
- Restrict COD for New Customers: Introduce fraud barriers during initial, high-risk transactions. First-time buyers might have COD limits of ₹2,500 until successful delivery or require phone verification for any COD orders. Once a positive history is established, these restrictions can be automatically lifted. This tactic acknowledges that fraud often targets first orders, where brands lack behavioral data, while repeat customers demonstrate reliability.
- Utilize Geographic Risk Segmentation: Calibrate COD availability based on area-specific fraud rates. Pin codes with fraud rates exceeding 15% could face enhanced verification, COD value limits, or temporary restrictions, while low-fraud areas retain full COD access. This localized approach protects brand economics in vulnerable regions without inconveniencing customers in low-risk areas. Continuous monitoring is essential as fraud operations can shift geographically.
- Incentivize Prepaid Migration: Strategically offer prepaid discounts to high-risk segments to reduce fraud exposure and improve unit economics. Providing ₹150-200 prepaid discounts to new customers or high-risk profiles effectively encourages them to choose prepaid options. The cost of these discounts is typically less than potential fraud losses and also enhances the customer experience. Many customers who accept these incentives tend to become habitual prepaid users, leading to a permanent reduction in brand fraud exposure.
How should brands respond when fraud is detected post-dispatch?
Recovery strategies and account management protocols balance loss minimisation with legal compliance
Immediate courier interception for confirmed high-confidence fraud cases can prevent delivery completion before packages reach final disposition. Most courier partners support shipment holds or return-to-origin requests for in-transit packages when fraud evidence emerges. This requires rapid detection and decisive action—waiting for delivery attempts wastes the narrow intervention window. Successful interception recovers 67-73% of product value through inventory return versus total loss from completed fraudulent delivery.
Account deactivation and related network blocking prevents repeat fraud attempts through identified fraudulent channels. Flagging phone numbers, email addresses, and delivery locations associated with confirmed fraud creates defensive perimeter blocking future orders from same sources. The challenge lies in avoiding collateral damage—shared addresses like apartment complexes or office buildings might block legitimate customers. Implement account blocks at individual account level whilst treating shared addresses as risk factors requiring verification rather than automatic blocking.
Legal documentation for systematic fraud operations justifies police complaints and creates deterrent signals. Organised fraud rings targeting brands repeatedly warrant formal action including FIRs documenting financial impact, evidence compilation showing coordinated activity, and engagement with cybercrime cells. Whilst recovery chances remain limited, visible legal responses deter future attempts by raising perceived risk. Brands should pursue legal action for cases exceeding ₹50,000 cumulative loss or demonstrating clear organised patterns.
Loss recovery through courier liability claims applies when fraud occurs despite courier negligence in verification protocols. If delivery was completed without collecting payment despite COD instructions, or packages were handed over without recipient verification, courier partners bear financial responsibility. Document these violations meticulously and pursue claims aggressively. Recovery rates hover at 40-60% for valid claims, partially offsetting fraud losses whilst incentivising courier compliance with verification protocols.
What data sharing and industry collaboration reduce fraud ecosystem-wide?
Collective intelligence networks prevent fraud migration across brands and enable coordinated defence
Industry fraud databases pooling confirmed fraud indicators across multiple brands create network effects in detection. When Brand A identifies a fraudulent phone number or address pattern, sharing that intelligence enables Brands B, C, and D to block related attempts proactively. Platforms like Fraud.net or industry associations maintain shared blacklists whilst preserving competitive information confidentiality. Participation in these networks improves detection by 28-35% beyond individual brand capabilities.
Courier partner collaboration sharing delivery-level fraud signals enhances detection through combined visibility. Couriers encounter refusal patterns, address issues, and customer behaviour at delivery moment that brands never see. Systematically feeding this ground-truth data back to brands enables pattern recognition impossible from order-placement data alone. Establishing formal data-sharing agreements with logistics partners creates fraud detection advantages whilst improving courier fraud awareness and prevention motivation.
Payment gateway fraud intelligence integration leverages transaction-level signals from financial institutions. Gateways processing millions of transactions daily develop sophisticated fraud detection identifying compromised cards, suspicious transaction patterns, and high-risk accounts. Brands accepting prepaid orders benefit from these gateway protections automatically, but COD-heavy brands can still access gateway fraud scores for risk assessment during checkout even when payment hasn't occurred. This cross-channel intelligence improves COD fraud detection by 18-24%.
Law enforcement coordination through formal channels or industry associations creates legal consequences that technological prevention alone cannot achieve. Cyber crime police stations in major metros increasingly recognise e-commerce fraud patterns, but require organised evidence from brands documenting systematic losses. Industry groups aggregating fraud data across members build more compelling cases than individual brands. Successful prosecutions create deterrent effects reducing fraud attempts industry-wide by raising perceived risk among fraudster communities.
Quick Wins
Week 1: Fraud Baseline Assessment and Rule Creation
Extract last 90 days of COD orders including customer details, order values, addresses, and delivery outcomes. Calculate RTO rates overall and for new versus repeat customers, high-value versus low-value orders, and different geographic segments. Identify orders exhibiting obvious fraud indicators: multiple orders same day to different addresses, high-value first orders, suspicious address patterns. Build initial rule-based scoring system assigning points for 8-10 key fraud indicators. Expected outcome: Quantified fraud baseline showing ₹XX monthly losses with implemented scoring framework ready for live deployment.
Week 2: Risk-Based Verification Implementation
Deploy OTP verification for orders scoring 40+ fraud points, focusing on new customers with high-value COD orders and suspicious address patterns. Integrate phone verification API (providers like MSG91, Kaleyra, or Twilio) triggering OTP sends during checkout. Monitor completion rates and impact on conversion for verified versus non-verified segments. Implement basic velocity controls: maximum 2 COD orders per phone number within 24 hours. Expected outcome: 35-45% of high-risk orders successfully verified with 75-82% of fraud attempts prevented at checkout stage, conversion impact limited to targeted high-risk segment.
Week 3: Address Validation and Enhanced Monitoring
Integrate Google Maps API or postal validation service checking address validity during checkout. Flag orders with unverifiable addresses for manual review before dispatch. Implement real-time fraud dashboard showing daily high-risk orders, verification completion rates, and orders held for review. Train operations team on fraud indicator recognition and verification call protocols for manual review cases. Expected outcome: 28-35% of address-based fraud attempts blocked through technical validation, with manual review process handling 20-30 daily edge cases requiring human judgment.
Week 4: Machine Learning Preparation and Continuous Improvement
Begin collecting structured fraud data—confirmed fraudulent orders marked in systems with detailed indicator documentation. Establish data pipeline feeding order characteristics, customer behaviour, and fraud outcomes into centralised database for future ML training. Analyse first three weeks of verification data identifying which indicators most strongly predicted actual fraud. Refine scoring model weights based on observed correlations. Document 5-7 fraud case studies for team training and pattern recognition improvement. Expected outcome: 12-week dataset collection initiated for ML model training, refined rule-based system with 68-74% fraud detection accuracy operating as interim solution.
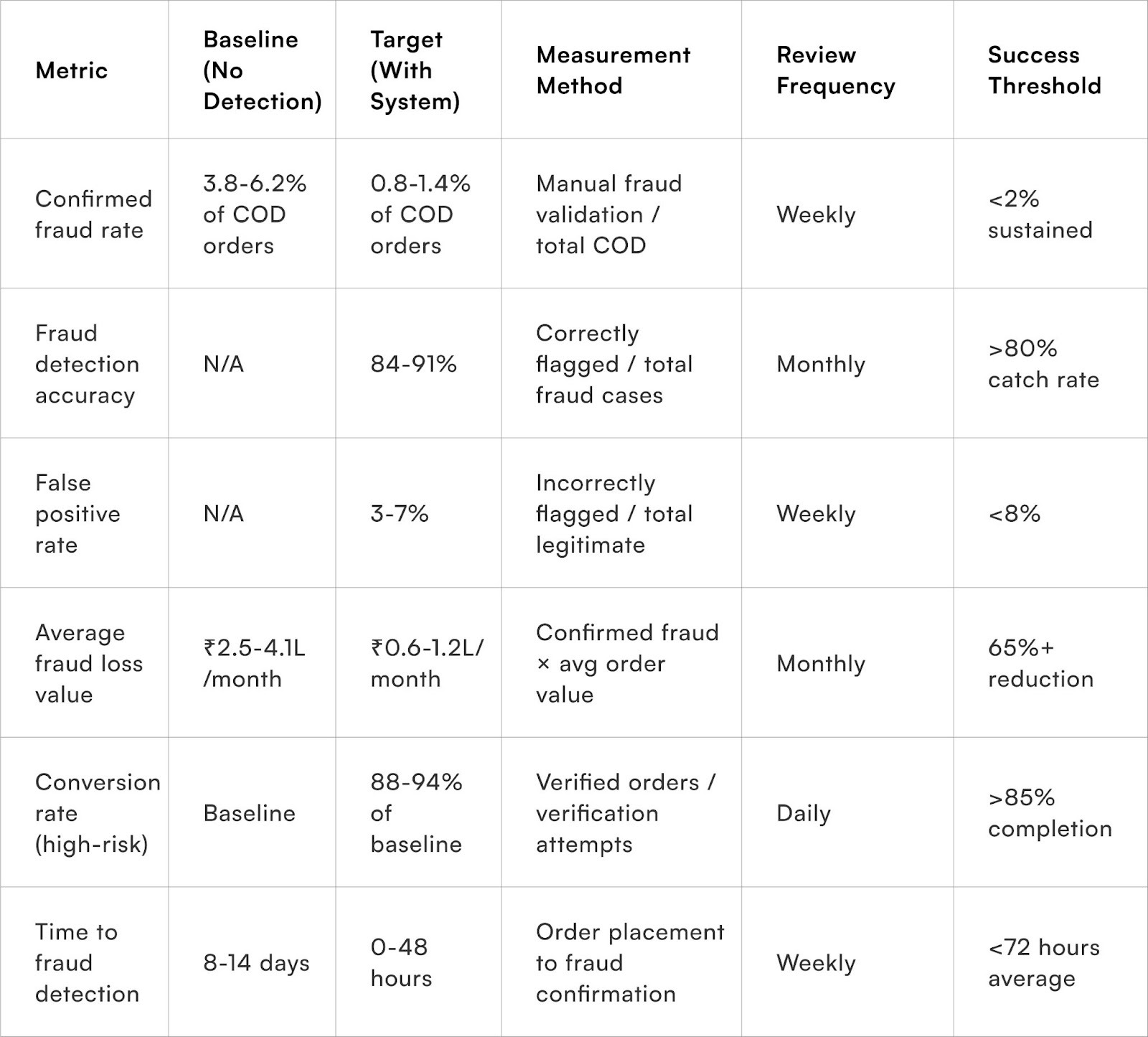
Measuring Fraud Prevention Effectiveness
To Wrap It Up
COD fraud represents persistent operational challenge requiring systematic detection, prevention, and response frameworks rather than reactive incident handling. Technology-enabled risk assessment combined with proportional verification intensity protects revenue whilst preserving customer experience and market access essential for growth. The most successful approaches treat fraud prevention as continuous improvement process adapting to evolving fraudster tactics rather than static rule application.
Conduct forensic analysis of your last 50 confirmed or suspected fraud cases to identify the three most common indicator combinations, then implement automated detection rules triggering verification for orders matching those specific patterns.
Long-term fraud prevention requires balancing multiple objectives: minimising losses, maintaining conversion rates, preserving legitimate customer experience, and adapting to evolving fraud sophistication. Brands investing in machine learning capabilities, participating in industry intelligence networks, and continuously refining detection models based on ground-truth feedback achieve 23-31% additional fraud reduction in year two beyond initial system deployment. The cumulative effect of systematic improvement compounds into sustainable competitive advantage through superior unit economics and operational efficiency that fraud-plagued competitors cannot match.
For D2C brands seeking comprehensive fraud protection without conversion sacrifice, Pragma's intelligent fraud prevention system provides real-time risk scoring, automated verification workflows, machine learning detection models, and industry intelligence integration that help brands achieve 68-76% fraud reduction whilst maintaining 88-94% conversion rates among verified high-risk orders through surgical intervention targeting actual threats while preserving experience for legitimate customers.

FAQs (Frequently Asked Questions On COD Fraud in Indian E-commerce: How to Detect and Prevent It)
1. What are the most common patterns of COD fraud in India?
COD fraud typically appears as fake or prank orders, high-value first orders from new accounts, multiple recent cancellations, mismatched addresses and phone numbers, and bulk orders targeting high-RTO pincodes or late-night time slots.
2. Is phone number or address verification effective for COD fraud prevention?
Yes—using OTPs, phone/email validation, and auto-confirmation via WhatsApp catches fake intent early, with many fraudsters abandoning orders after a verification step. Smart workflows pause shipment until details are confirmed, especially for new or high-risk customers.
3. What role do regional and customer profiles play in COD fraud?
COD cancellation rates can reach 45% in tier-3 cities and 35% in some eastern regions, while tier-1 cities are often less risky. Brands use machine learning to assign dynamic COD limits by region, risk score, or customer cancellation history for tighter control.
4. Should brands fully disable COD to prevent fraud?
Rarely. Blanket bans slash new customer acquisition and revenue. Instead, combine COD risk scoring, partial prepaid or token payments, and smart nudges—like incentives to prepay or limiting COD for repeat violators—to protect margins without penalising genuine buyers
Talk to our experts for a customised solution that can maximise your sales funnel
Book a demo




.png)